In the face of multiple, repeated and increased cybersecurity attacks, the US president ordered the federal organizations to beef up their security, through Executive Order on Improving the Nation’s Cybersecurity Executive Order on Improving the Nation's Cybersecurity | The White House
One of the key requirements to the federal agencies was to “develop and issue (….) a cloud-service governance framework. That framework shall identify a range of services and protections available to agencies based on incident severity. That framework shall also identify data and processing activities associated with those services and protections.”
Ok, but that is the US government, with almost unlimited resources. What can be done by you, the CEO of a small or medium enterprise?
Well, you should inspire yourself from, and reuse the work that that the government agencies did for themselves, use the public frameworks and materials and adapt them for yourself. For example, you can use the National Institute of Standards and Technology ( NIST) CyberSecurity Framework – CSF ( known as publication 800-53) as the foundation for the implementation of a Cyber security program in your enterprise.
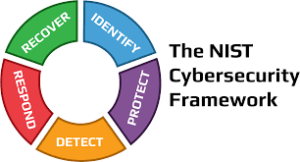
The NIST CSF organizes the cybersecurity approach thinking and controls around 5 main functions:
You can start an assessment of your current CyberSecurity status using the NIST CSF framework questionnaire here
Or you if you find it too long or complicated, you can use the summary questions below:
IDENTIFY
Asset Management (ID.AM): What are the most important information assets of the organization, and how are they classified and prioritized based on their value and sensitivity?
Business Environment (ID.BE): What are the regulatory requirements and industry standards that impact the organization's cybersecurity posture, and how does the organization's business context influence its cybersecurity risk management strategy?
Governance (ID.GV): How is the organization's cybersecurity governance structure designed and implemented, and what resources and budget are allocated to support it?
Risk Assessment (ID.RA): What are the most significant cybersecurity risks facing the organization, and how are they identified, evaluated, and monitored over time?
Risk Management Strategy (ID.RM): What is the organization's overall cybersecurity risk management strategy, and how is it aligned with the business strategy and risk appetite?
Supply Chain Risk Management (ID.SC): What are the third-party suppliers and service providers that the organization relies on for its operations, and what are the potential cybersecurity risks associated with these relationships, and how are these risks managed?
PROTECT
Access Control (PR.AC): How is access to information assets and systems controlled, and what authentication and authorization mechanisms are used to ensure that only authorized users and processes can access them?
Awareness and Training (PR.AT): How is cybersecurity awareness and training provided to employees, contractors, and other stakeholders, and what topics and frequency are covered in these programs?
Data Security (PR.DS): How is sensitive data identified, classified, and protected, and what encryption, backup, and retention policies are in place to ensure its confidentiality, integrity, and availability?
Information Protection Processes and Procedures (PR.IP): How are security policies, standards, guidelines, and procedures developed, approved, and communicated throughout the organization, and what is the process for managing exceptions and deviations from these policies?
Maintenance (PR.MA): How are information systems, software, and hardware maintained and updated to ensure their security and reliability, and what are the procedures for testing and verifying these updates?
Protective Technology (PR.PT): What protective technologies are used to secure information systems and data, and how are they selected, implemented, and configured based on the organization's risk management strategy and cybersecurity requirements?
DETECT
Anomalies and Events (DE.AE): How are potential cybersecurity events and anomalies identified, and what tools, techniques, and procedures are used to monitor and detect them?
Security Continuous Monitoring (DE.CM): How is the organization's cybersecurity posture continuously monitored and assessed, and what is the process for identifying, reporting, and responding to cybersecurity incidents?
Detection Processes (DE.DP): What detection processes are in place to identify potential cybersecurity incidents, and how are these processes tested and improved over time?
Event Analysis (DE.EA): How are cybersecurity events analyzed, and what criteria are used to determine their severity and impact on the organization's assets and operations?
Incident Response (DE.IR): What is the organization's incident response plan, and how is it activated, tested, and improved over time to ensure that cybersecurity incidents are managed effectively?
Mitigation (DE.MT): How are cybersecurity incidents mitigated, and what measures are taken to minimize their impact on the organization's assets and operations?
RESPOND
Response Planning (RS.RP): What is the organization's incident response plan, and how is it developed, tested, and updated to ensure its effectiveness in responding to cybersecurity incidents?
Communications (RS.CO): How is communication managed during cybersecurity incidents, and what is the process for coordinating and sharing information with internal and external stakeholders?
Analysis (RS.AN): How are cybersecurity incidents analyzed and evaluated to determine their impact and scope, and what tools and techniques are used to conduct this analysis?
Mitigation (RS.MI): What measures are taken to contain and mitigate cybersecurity incidents, and how are these measures coordinated with other response activities?
Improvements (RS.IM): What improvements are made to the incident response plan and process based on lessons learned from previous incidents, and how is this process integrated with the organization's risk management and continuous improvement programs?
RECOVER
Recovery Planning (RC.RP): How is the organization's recovery plan developed, tested, and updated to ensure that critical systems and data can be restored quickly and effectively in the event of a cybersecurity incident?
Improvements (RC.IM): What improvements are made to the recovery plan and process based on lessons learned from previous incidents, and how is this process integrated with the organization's risk management and continuous improvement programs?
Communications (RC.CO): How is communication managed during the recovery process, and what is the process for coordinating and sharing information with internal and external stakeholders?
Service Continuity (RC.SC): How is service continuity maintained during the recovery process, and what measures are taken to ensure that critical functions can be restored as quickly as possible?
Recovery and Reconstitution (RC.RR): How are systems and data recovered and reconstituted after a cybersecurity incident, and what measures are taken to ensure that the recovered systems and data are secure and functional?
Post-Incident Activities (RC.PA): What post-incident activities are conducted, such as forensic analysis and damage assessments, and what improvements are made to the organization's cybersecurity posture based on the results of these activities?
Ready to find out more?
If you still find it difficult to navigate all the assessment questions, please drop us a line, we can help you out!