Currently affected by security breach?
Containement
Swiftly containing the cybersecurity incident to prevent further damage and spread of the threat.
- Isolation: Move, and isolate affected devices to CollabPro secure network infrastructure in order to prevent the spread of the threat.
- Access Control: Restrict access to critical systems and resources to authorized personnel only.
- Network Segmentation: Implement segmentation to isolate the compromised parts of the network from the rest.
- Endpoint Protection: Employ measures to secure endpoints, ensuring that compromised devices do not pose additional risks.

Analysis
In-depth analysis is conducted to understand the nature of the cyber threat, live traffic scan using pattern and signatures of cyber attacks.
- Threat hunting: Conduct a thorough examination of live traffic to gather evidence and understand the scope of the incident.
- Vulnerability Assessment: Identify and address vulnerabilities that may have been exploited during the incident.
- Incident Documentation: Document all findings, including timelines, actions taken, and potential indicators of compromise.
Detection and Reporting
Continuous monitoring is implemented to detect any residual threats and potential reoccurrences, preventing lateral movement within the network.
- Real-time Monitoring: Implement continuous monitoring to detect any unusual or suspicious activities within the network.
- Anomaly Detection: Use advanced tools to detect anomalies in system behavior that may indicate ongoing threats.
- Alerting and Reporting: Establish mechanisms for real-time alerts and regular reporting to keep stakeholders informed of the ongoing detection efforts.

What is CyberFerry?
- Rapid restore of network and Internet connectivity during a cybersecurity incident.
- Temporary connectivity workaround - Implementation of a secure channel and network infrastructure to connect to your cloud services in the containment phase of a cybersecurity incident.
Insert CyberFerry in your CyberIncident Response plan.
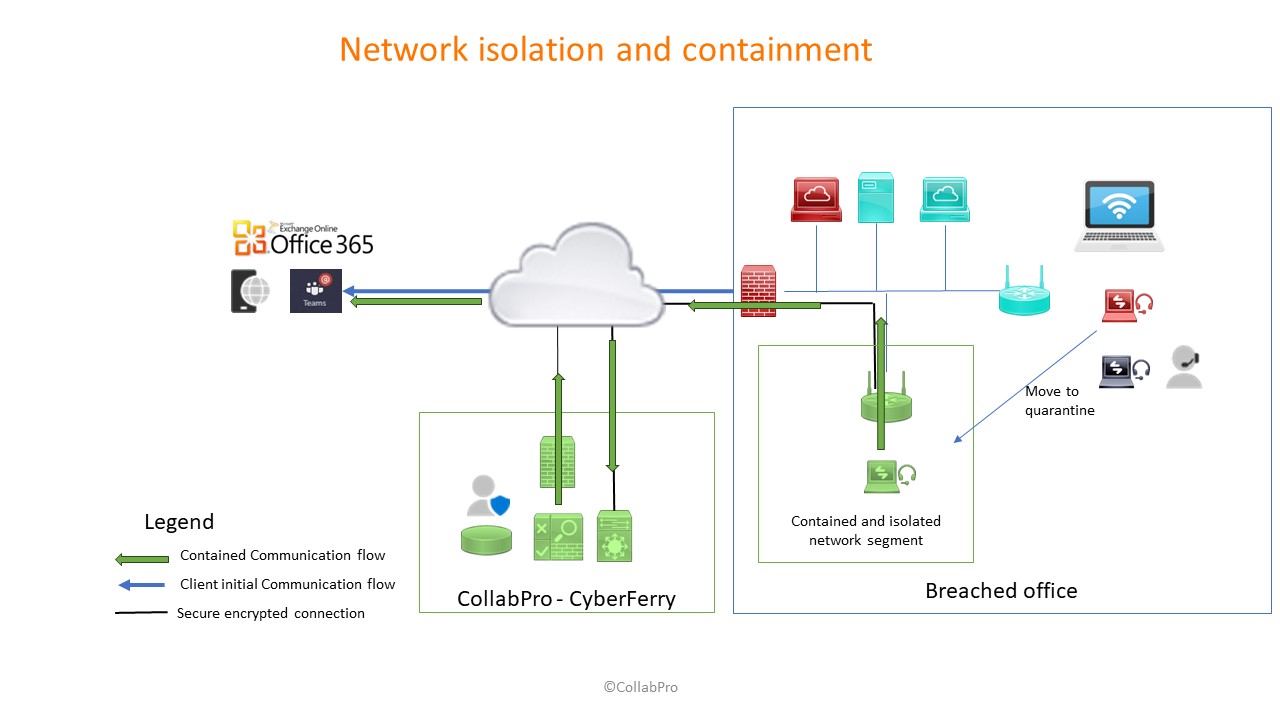
How it works
Your users will switch the network connection to a CyberFerry which routes all the traffic through a network cleaning service reachable via Internet. Once all traffic has been inspected and deemed safe, the packets are routed to their final destination (Cloud Services, being Office 365, Teams, Sharepoint, Onedrive etc.)
No additional software is installed on the laptops, intelligent phones or client’s network devices.
Why CyberFerry
It took an average of 204 days to identify a data breach, globally (IBM).
Some times antiviruses are not able to detect and prevent all attacks on user endpoints ( laptops, intelligent phones). Even worse, IoT devices can be subject of different cybersecurity attacks, no antivirus is available for this scenario.
The average time to contain a breach was 73 days (IBM).
Once a breach has been declared the full network becomes quarantined. Workstations and users should stop connecting to cloud services, otherwise the files and services located in the cloud would risk infection (malware, ransomware, etc). The Client’s cyber incident team should clean workstations one by one and connect them to the new network provided by the access point, thus, migrating the traffic through CyberFerry gateway for deep packet inspection and signature attack recognition.
Collabpro will begin a secondary detection and analysis phase of the incident, reporting and flagging any other detected suspicious traffic for the migrated workstations, preventing the lateral attacks and spreading of the infection. This procedure will allow the client’s cybersecurity team to advance the eradication phase of the cybersecurity incident and focus on the endpoints and network devices that are still on the old network, trying to repair the breach damages while documenting and preserving legal evidence.
