This article is written for the CyberSecurity responsible person working for a small enterprise, willing to start or advance their company Cybersecurity program.
So, you read all the documents and presentations for the NIST CSF and you master all the 5 functions.
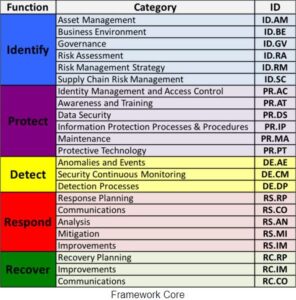
And you understand how mapping all these 5 functions, 23 categories and 108 subcategories to, maybe, existing controls. While this seems to be a long list of categories and subcategories, the secret is that maybe not all of those apply to your business.
An example of function/category/subcategory is listed below
Remember, the list of controls will not tell you how well you do and execute those controls.
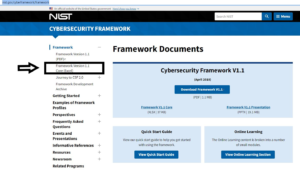
Start simple, download the categories list from the NIST web site
Make CSF your own: Once downloaded, open the excel file and add two columns: Tiers and Priority. DO not over complicate.
You are ready to sit down with business and IT representatives and complete the excel file.
Tiers, you already know what is the CSF definition, link here: https://csf.tools/reference/nist-cybersecurity-framework/v1-1/#framework-implementation-tiers
Avoid analysis paralysis. I propose couple of simple questions to help you determine the existing tiers to be documented for each of the categories. Tiers are a qualitative measure of organizational cybersecurity risk management practices.
Tier 1: Partial
Have you communicated the importance of cybersecurity to your business?
Has your business begun to follow basic cybersecurity best practices?
Tier 2: Risk Informed
Are you implementing a leadership-driven, company-wide cybersecurity program?
Have you integrated cybersecurity with risk management processes?
Tier 3: Repeatable
Are you evaluating your cybersecurity posture and capabilities?
Are you participating in an information sharing forum to gain insights and strategies?
Tier 4: Adaptive
Have you trained your staff to prevent, detect, and respond to cyber incidents?
Are you utilizing cyber defense technologies to support your operation?
Once the Tier column is populated in the excel file, you are ready to attack the Priority column, that should be the equivalent of the Profile discussion around the timeline and the roadmap for reducing gaps between the organizational goals and the potential cyber risk to associated with these goals
Remember, not all categories and subcategories should be Tier 4. Tier 4 is very expensive, and it should not be your absolute goal.