Cloudflare Tunnels is a free alternative to traditional VPNs which usually require and advanced firewall as well as client VPN installation and configuration.
This article discusses the advantages of using Cloudflare Tunnels to provide external access to internal services and applications.
Cloudflare Tunnels allows external users to connect to internal resources (any internal service on your private network with a web interface) without poking holes in the firewall or exposing your own public WAN IP address. Additionally, Cloudflare Tunnels can create secure HTTP connections to devices and
services that don't provide a secure interface, and it can work with internet connections that only hand out CarrierGrade NAT.
Cloudflare Tunnels offers significant advantages over traditional VPNs and we predict that this technology will become more popular in the coming years.
Moreover, the following features can enable you small business to get closer to achieving Zero Trust architecture requirements:
- Avoid the recurring cost of an SSL certificate if you so chose to place your web server behind
cloudFlare - Secure your webservices by allowing inbound connectivity based on allowed geografies.
geolcation based access. - Add multifactor authentication(MFA) to your web portals. Through CloudFlare, you can impose one time password access or a secondary gmail (linkedIn, Facebook, etc) authentication before getting to your web portal server authentication page.
- You can save Internet traffic cost for your virtual servers hosted on platforms like Azure or Amazon using the free outbound-only connection feature of CloudFlare.
Here you have some high level steps required for the CloudFlare tunnels implementation:
- Acquisition and configuration a public DNS domain name that you can use with Cloudflare.
- A Cloudflare account (free)
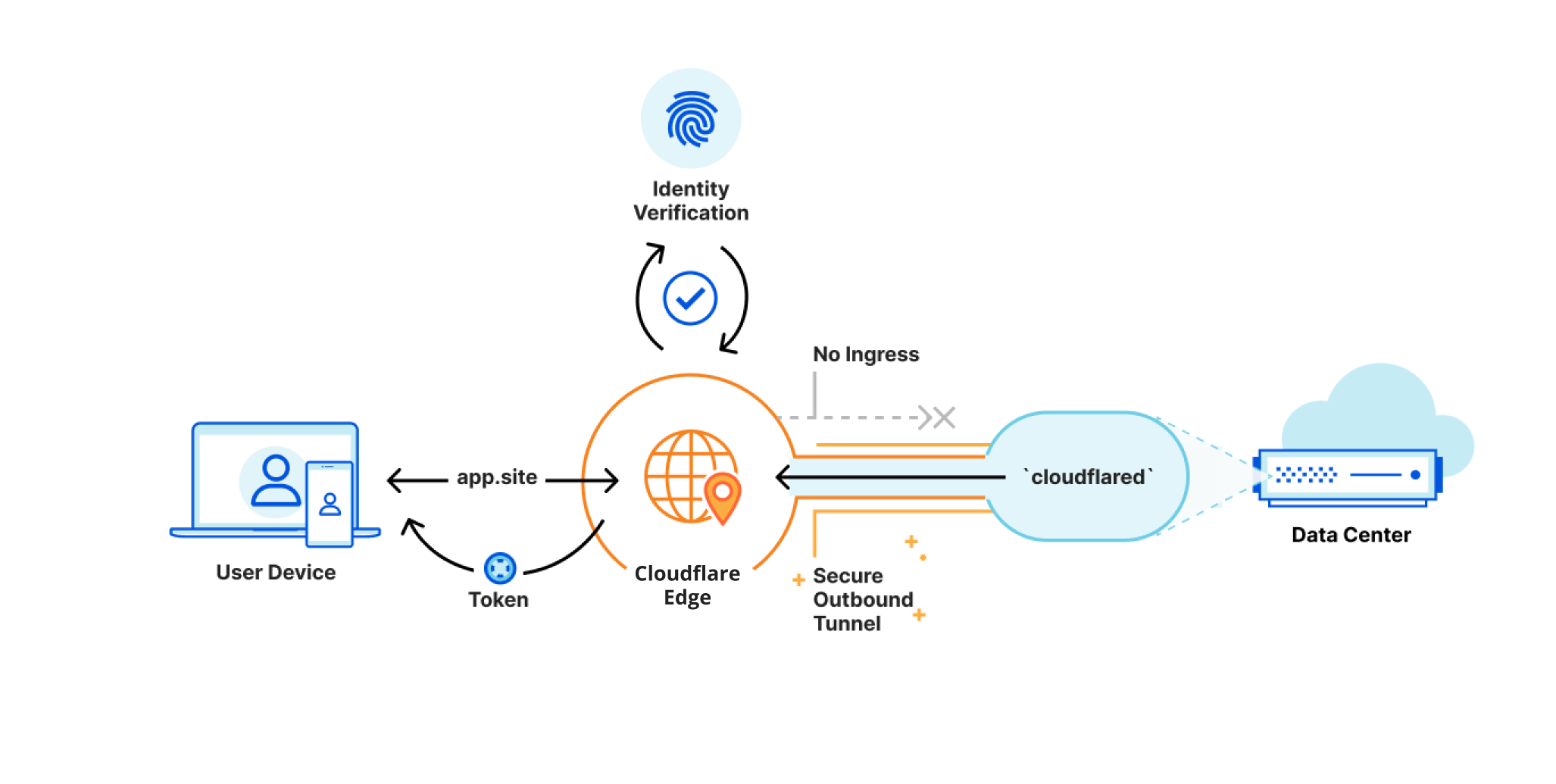
- Cloudflare connector on your LAN (see cloudflared in the image below). This is a piece of
software that you will need to download and install on a server on you local network. An easy alternative is using Docker on a NAS to set up the Cloudflare connector, as it is lightweight and easy to manage through Cloudflare's GUI-based Zero Trust dashboard. Cloadflared will initiate
the connection the connection to CloudFalre cloud via Internet and once authenticated it will esatblish an encrypted tunnel between the CloudFlare Edge and your internal Network.
CollabPro can help your Zero Trust implementation, give us a call in order to help you improve your business security posture.
Here you have some high level steps required for the CloudFlare tunnels implementation:
- Acquisition and configuration a public DNS domain name that you can use with Cloudflare.
- A Cloudflare account (free)
- Cloudflare connector on your LAN (see cloudflared in the image below). This is a piece of
software that you will need to download and install on a server on you local network. An easy alternative is using Docker on a NAS to set up the Cloudflare connector, as it is lightweight and easy to manage through Cloudflare's GUI-based Zero Trust dashboard. Cloadflared will initiate
the connection the connection to CloudFalre cloud via Internet and once authenticated it will esatblish an encrypted tunnel between the CloudFlare Edge and your internal Network.
CollabPro can help your Zero Trust implementation, give us a call in order to help you improve your
business security posture.
