You are the owner of a small business. Something bad happens to your organization, like the accountant and finance clerks cannot process invoice payments because their computer system got so slow or it is unusable. What do you do?

That kind of situation is called an IT incident.
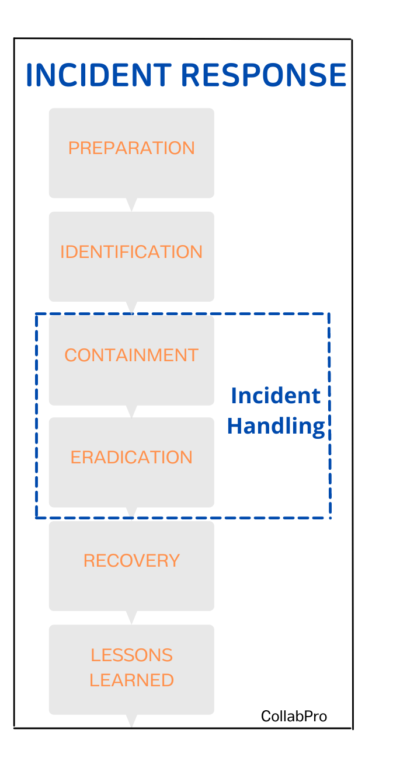
If your organization did their homework, you
already know it is an incident:
- You know how to define an incident (what it is an incident and what it is not)
- You know how to qualify it (what is the scope of what is working or not, what is
affected, how serious it is, is it affecting your internal operations only or it affects
also your customers).
Once the incident has been identified and declared, you need to HANDLE it:
- Who do you need to call, contact
- When do you need to call
- Are there any government regulation requirements for the handling of the incident
(communications, data preservation)?
- Should your insurance company be involved? At what point?
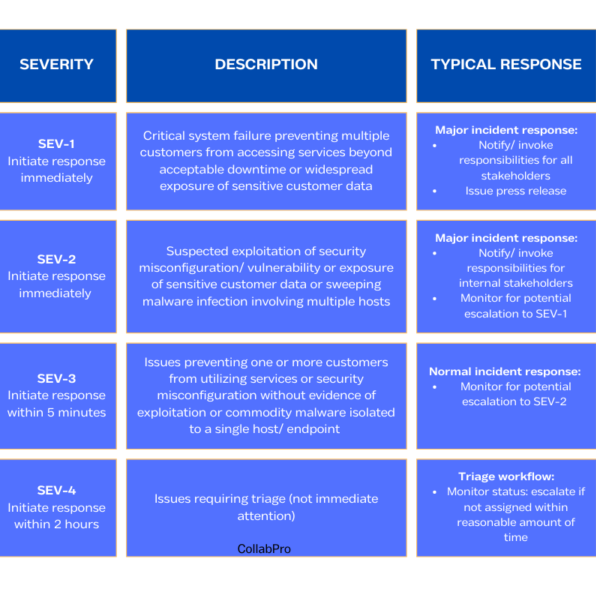
Once the response plan is in place, your actions can be grouped in 3 major phases:
Contain the threats
- Your incident response team (internal or external) will engage with the affected hosts and
elements of your IT system. - Prevent further damage and inhibit the attackers to spread their control on additional network
assets.
Eradicate the threats
- This typically takes care of removing the threat from the environment.
- Remove malicious code, rebuilding endpoints.
Recover
- This phase takes care of the restoration of services and functionalities so the return to normal
operations can be competed. - Actions like, re-imaging a PC, reinstalling servers, restoring iPhone configuration are required.
It can also mean replacing a high-risk vendor.
CollabPro advises and helps customers improve their IT security posture:
- IT systems configuration decisions
- Review and recommendations on existing Incident Response plans
- Choice of automation tools required to support your incident response capabilities.
